Cyber threat hunters proactively cull through endless amounts of data to determine if there has been an intrusion on a network and create hypotheses about potential threats. They have their work cut out for them with research finding that in 2021, the average number of cyberattacks and data breaches increased by 15.1% from the previous year. Unfortunately, the problem is only expected to get worse with estimates predicting attack rates to double by 2025.
Download Primer’s Guide to NLP Use Cases
But computer networks aren’t the only targets. Operational technology like systems that control utilities, railroads, aviation, hospitals, and other critical sectors are being targeted. Several high profile attacks showcase these ominous statistics and attack vectors. The Russian hacker group Killnet recently claimed responsibility for a DDoS attack on Lithuania, stating they’ve “demolished 1652 web resources.” And North Korea state-sponsored cyber actors have targeted the healthcare sector using ransomware to hold health records hostage until they get paid.
Security analysts tasked with tracking cyber actors’ tactics, techniques, and procedures (i.e. TTPs) and attack trends need to have their finger on the pulse of cyber attack data. They need to monitor incoming information around the clock, anticipating any threats, and providing insights to their information security and information technology teams to help guard company assets and infrastructure.
Primer Command automates threat intelligence extraction
Primer Command’s natural language processing (NLP) algorithms automatically structure and summarize millions of news and social media posts across 100 languages to surface key people, locations, organizations, topics, suspected disinformation, sentiment, and media to better understand how a situation is evolving.
Command can take unstructured information, including threat intelligence posted online from advisories, and tag key entities that are mentioned. Often multiple sources detail the same threat intelligence, leading to wasted analyst time. By having this information organized, deduplicated, and summarized, cyber analysts will have more time to spot connections across threat vectors and actors.
The following puts a spotlight on the power of Command’s ability to zero in on the information that matters most to cyber threat analysts through advanced filters and AI-enabled classifiers.
Cyber attack filters
Command can filter on six types of cyber attacks to drill down into the information cyber threat analysts care about most. So instead of conducting keyword searches on multiple social media platforms and search engines to find the latest information on cyber threat attacks, analysts can strip out the noise and save time by getting the insights they need in one place.
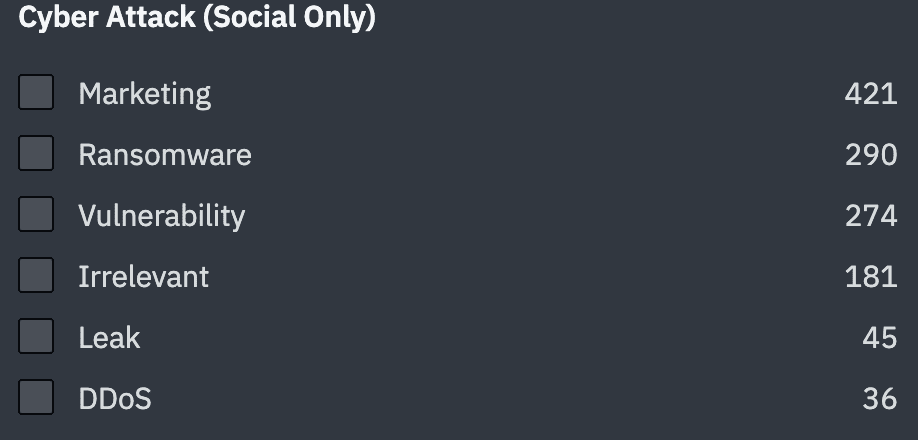
Taking a look at the Distributed Denial of Service (DDoS) attack on Lithuanian energy supplier Ignitis Group, security teams can learn more about the attack by filtering social media and news posts in Command by DDoS attack type. This instantly delivers reports about the Ignitis attack as well as other DDoS attacks that could be of interest to security researchers.
They can also learn what major cyber security firms report with organization filtering tags. They can isolate reporting from industry experts, like Proofpoint or Bleeping Computer, to learn their take on the DDoS attack or other attack vectors. In the same way, users can isolate reporting related cyber threat actors like Killnet or the Lazarus Group.
Infrastructure filters
Command’s advanced filtering capabilities allow cyber threat analysts to unlock critical information about ongoing or recent attacks on infrastructure. Command’s industry-leading NLP models accurately identify social media posts related to infrastructure, including companies and government organizations charged with managing and protecting these critical public goods.
For cyber threat hunters, this filter becomes more interesting when combined with cyber threat filters, like ransomware. With these combined filters, security teams can immediately see several social media posts about ransomware attacks on operating networks for companies or governments managing important public dependencies.
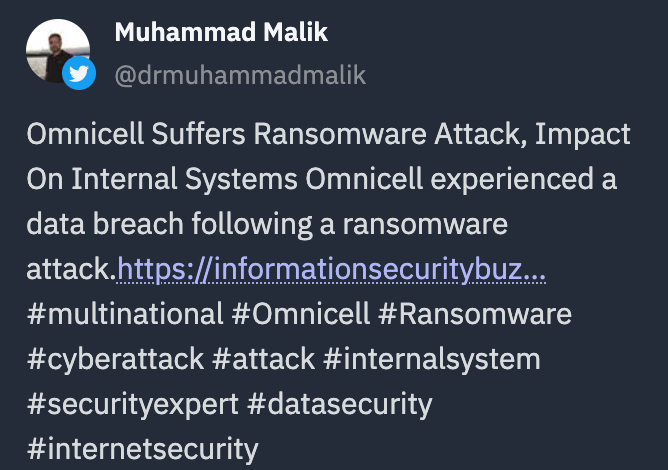
Organization extraction
By just looking at organization extractions, cyber threat analysts can quickly identify what the trending cyber attack victims and culprits are across multiple social and news media without having to read through all of them. Command’s extractions surface who the attacker or victim is, enabling cyber threat analysts to quickly see all the reporting related to these entities. In the screenshot above, “Omnicell” would bubble to the top as a victim or “Mantis Botnet” as an organization. Similar to above, this can be layered with other filters like type of attack.
Learn more
To learn more about Command’s other capabilities, click here for a free trial of Command for Tactical Insights. Contact sales to discuss your specific needs. You can also stay connected on Linkedin and Twitter.
We create the tools behind the decisions that change the world. ©2023 Primer



